This is complete step-by-step configuration instructions for setting up VPN connectivity (L2TP/IPSEC) between Zywall USG firewall and the client devices including Windows Phone, iPhone/iPad and Android or Win 10 OS.
For those not fully aware about the advantages VPN will give you – it will enable an encrypted pipeline to your home/office network, and you can use all the services/devices in your private network in safe and secure manner, without opening unnecessary ports that would increase the level of vulnerability of your private network.
Examples of VPN usage:
- Connect and use internet and online services in encrypted and secure manner from not-trusted environments like cafes and public WiFis.
- Stream freely from anywhere your private videos, view your private photos or work with any computer/document that is available in your network.
- View and access country-level regulated online materials from your VPN ‘home’ location when traveling abroad.
- Connect to you surveillance cameras, wildlife trail cameras or home alarm systems.
Find below step-by-step configuration instructions for enabling above:
Zywall:
1) Setup and ensure/add that ports required by VPN connectivity are defined and available (NO other SERVICES that are utilizing the same ports!):

2) Create VPN User (Object/User tab) and VPN Group (ObjectGroup tab), and add created user into the Group:
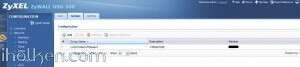
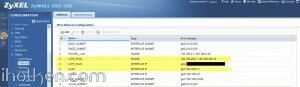
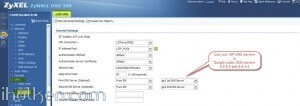
3) Create WAN, L2TP_POOL and LAN addresses accordingly (L2TP range TO BE completely outside any home/external IP range, that might be in use in either end of the VPN tunnel during VPN utilization – otherwise you may expect trouble…):
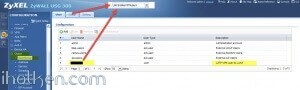
4) Create IPSEC VPN gateway (create own or utilize default available, link then to VPN connection created below):
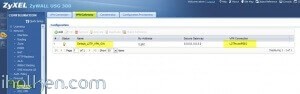
4) Detailed configuration example:
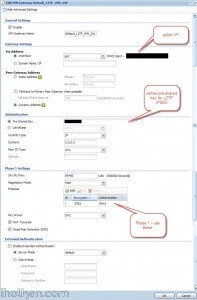
5) Create VPN connection that uses above created VPN gateway (you can utilize default available or create own):
5) Detailed configuration example:
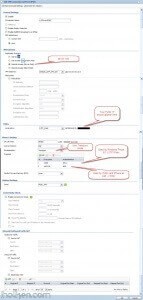
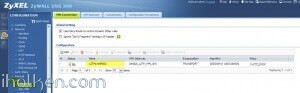
7) Create required firewall rules. Make sure VPN required services/ports are allowed (for example IKE, default rule in Zywall). Allow from IPSEC/VPN to LAN or to ANY, depending if wanted through VPN access only to LAN or also to internet:
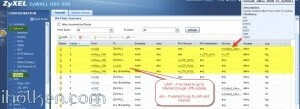
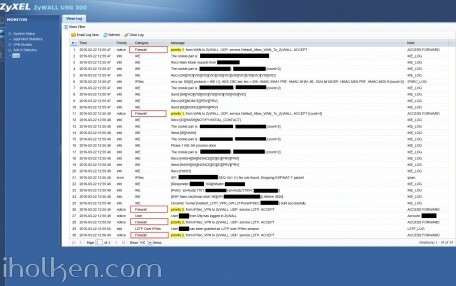
Firewall rules has critical role in establishing the tunnel and allowing the traffic through the tunnel. Please find below for VPN connection ‘negotiation handshake’ troubleshooting purposes an example of successful L2TP/IPSEC handshake flow extracted from Zywall log, and the parts where firewall rules play critical role:
If you have any issues with your firewall, please enable logging for correct steps and investigate the zywall logs – they are extremely useful.
8) Create required routing rules. (IF ‘send all traffic’ through VPN is on (meaning internet through VPN) – you also need to setup the Policy Route that is upper in the table below:
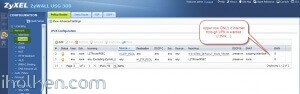
9) Keep WAN trunk and SNAT enabled:
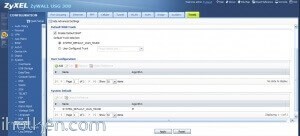
Client Machine:
10) Configure client machine – below example Windows Phone 8.1+:
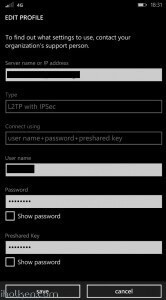
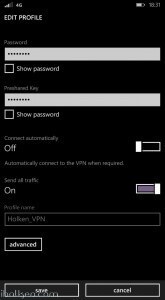
Test Connectivity:
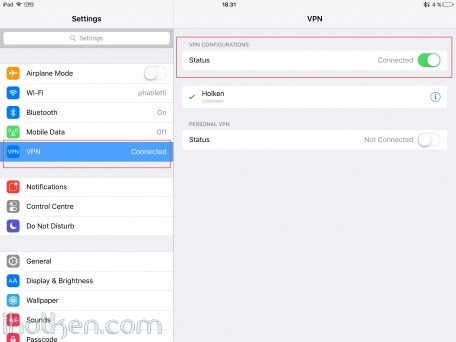
11) Test and confirm VPN by accessing your private network through 4G VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.

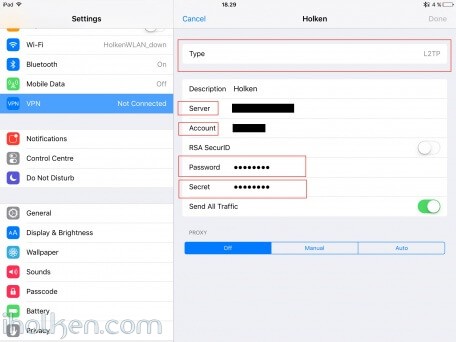
12) Configure client machine – below example for IOS (IPhone or IPad):
Test Connectivity:
13) Test and confirm VPN by accessing your private network through VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.
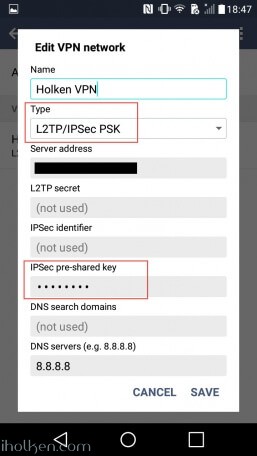
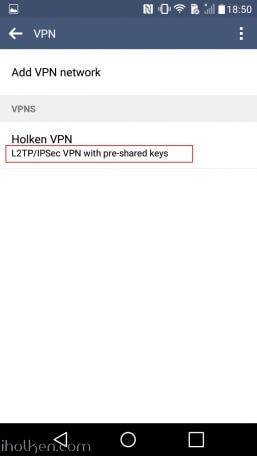
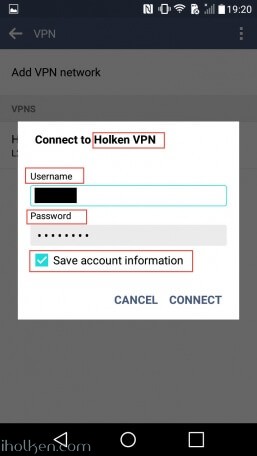
14) Configure client machine – below example for Android (Lollipop sw):
Test Connectivity:
15) Test and confirm VPN by accessing your private network through VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.
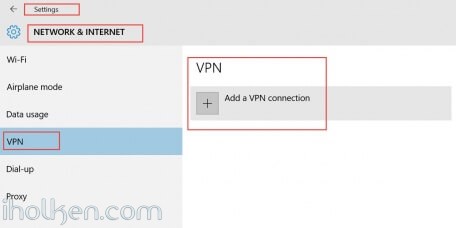
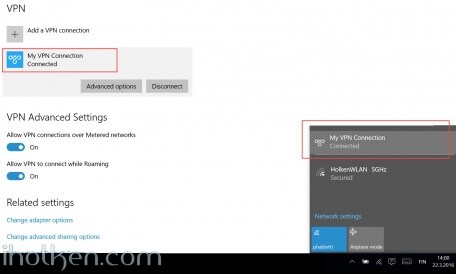
16) Configure client machine – below example for Windows 10 Operating System:
Navigate to: Start –> Settings –> Network & Internet –> VPN –> Add a VPN connection
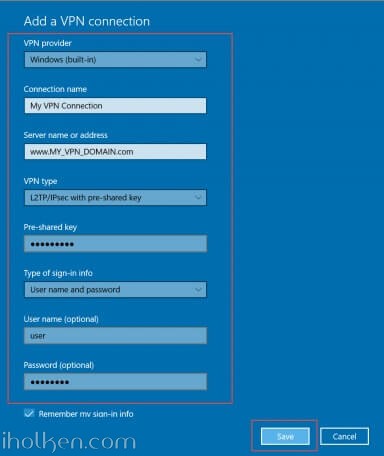
Then give the required connection details for the connection and hit Save:
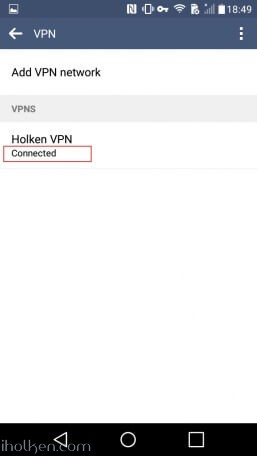
Now you are able to Connect to the VPN tunnel – through Network Settings or System Tray, and see ‘Connected’ indicator:
And that’s it!
Now you have configured the Zyxel Firewall for VPN connection with L2TP/IPSEC and client device being WP or IOS / Android Device or Win10 OS.
If this helped you in getting your VPN connection built, please drop me a post below for confirmation – Thanks!!! 🙂





Hi,
I followed your guide step by step but I’ve this error when I try to connect from android to vpn Zywall 40USG ( Firmware V4.20(AALA.2)
-looking up IPSec SA for the L2TP tunnel
– no IPSec protection for L2TP tunnel
– L2TO [Responder, incoming-call] negotiation failed.
What could it be ??
Thank for your help
Giorgio
The same problem, after the update for 4.20
Dear Juha Ketola,
thank you very much for your very detailed how-to. My VPN works perfectly. Just awesome your step by step guide!!!
Now, I want to connect with my IP security cam, which is only reachable in my LAN. Unfortunately, I can’t connect to my cam (with local LAN1 subnet IP- Address) via VPN (HTTP PORT 88). In my LOG, I can see, that the Firewall allows the request. Therefore, I guess I should configure some Routing (Policy Routing), like
Incoming: VPN L2TP connection
Source L2TP VPN pool
Destination: IP-Address of my IP Cam
Next Hop ?
SNAT ?
Do you have any idea or recommendations?
Thank you very much for your help!
Highly appreciated.
Thanks
John
Hey John,
Thanks!!!
I assume you try to reach your camera UI directly through LAN IP, as it would be on your LAN?
That should not need any routing… just make sure you allow in your firewall the traffic (all service ports) from VPN to that LAN network where your cam is – and you are all set.
No routes needed for this, you are having VPN tunnel to your LAN, and that means you are able to browse LAN devices directly If you have allowed that in your firewall….
Thanks for your fast reply.
Yes correct. I want to reach the Camera UI with my Local IP
The firewall rule is #4,#5 in your example or?
In the LOG, I can see ACCESS FORWARD, if I enter the Camera Local IP on the VPN device.
thanks
john
Hi,
Correct, rule 4 or 5.
Are you saying you do get access forward on log from VPN to LAN when reaching camera, but still you do not reach camera UI?
THAT is interesting….. What is the error on screen / zywall log?
You can always create an temporary ALLOW firewall rule just for your camera as rule 1, and put full logging on on your zywall to see If you reach the camera or not. And this way work through the flow to understand where the issue is…
Are you sure you are not having some additional configurations on your zywall? Like routes etc.
My setup described here works fine with cameras through VPN, i have the same setup myself.
Hello Juha,
I solved my issue. I just added one Routing line before your routing line 1 (which is needed for internet with System Default WAN Trunk)
Therefore, I have included routing:
Incoming VPN L2TP connection
Source VPN IP Pool
Destination LAn1 Subnet
Next Hop AUTO
SNAT none
Gr8 to hear!
Although I still really can’t figure out why you need it. There has to be something special in your setup…
But most important thing is that it is working now!!
Take care!
Hi
This is best how-to for zyxel what i have seen !
It really works, i used USG-40 with latest firmware, but i still have one problem,
Network mapping works from win, android and iPad client but not from Mac os Sierra.
Tunnel opens ok but nothing after that
Can you help me with this one ?
Hi Arto,
If your setup is working fine from those 3 clients, but not from Mac os Sierra….
I really would like to blame the Sierra for your problems….
What you actually mean by saying:”tunnel opens ok, but nothing after that?”.
Have you investigated the zywall logs, or Sierra logs for any entries in relation to your issues?
It is in practice very hard to help with the info you provided about this….. sorry
Hi Juha,
thanks for your guide. I have never configured a Zywall before, and this has really helped me .
I follow your guide step by step a lot of time and reset zywall to default settings but android does not connect.
On first my zywall does not log when i try to connect from Win10 but it logs when I try to connect from
android .When I try to connect from Android (One Plus One) I have this error :
-looking up IPSec SA for the L2TP tunnel
– no IPSec protection for L2TP tunnel
– L2TO [Responder, incoming-call] negotiation failed.
From zywall log.
What could be the problem ?
My firewall is Zywall USG 40 with latest firmware Firmware V4.20(AALA.2)
Any help will be appreciated.
Best regards Giorgio
Hi,
Is it failing in phase1 already, or in phase 2 negotiation?
Please check the supported encryption settings for your client, and add there the needed encryption settings for phase 1 and phase 2 for your client. Hope this solves your problem, please let me know.
Br,
Juha
Hi Juha,
I think it fail during phase 1, but my zywall does not log all VPN operation. My log is completely different from your.
I tried all encryption combination but the problem persist, and the log is the same:
– looking up IPSec SA for the L2TP tunnel
– no IPSec protection for L2TP tunnel
– L2TO [Responder, incoming-call] negotiation failed.
May be some service is not started on Zywall ?
thank for your reply.
Giorgio
hi,
Please enable log in your firewall for each rule related to VPN connection. Then you also get the log rows needed for troubleshooting.
Hi , i try to setup this connection with a USG 20 firewall and windows 10 client but in the log i see this error :
Send:[HASH][NOTIFY:NO_PROPOSAL_CHOSEN]
[SA] : No proposal chosen
[ID] : Tunnel [Default_L2TP_VPN_Connection] Phase 2 Local policy mismatch
Recv:[HASH][SA][NONCE][ID][ID][PRV][PRV]
Phase 1 IKE SA process done
Hi,
Step 5) Detailed configuration example.
Please check your configuration for these parts. Are you using same encryption settings for phase2, and in same order? If for some reason these I present here is not working for you, you can try some other encryption settings for phase 2, like AES 256 etc. But these basically should work for you, they do work for me.
Hope this helps.
i am using :
phase 1: 3DES/SHA1/DH2
phase 2: 3DES/SHA1/none
i try all encryption combinations in phase 2 but … nothing
Out of all the different configuration guides including the ones from Zyxel, this one was the one that made it work. Still have some issues with Mac and forwarding all traffic as opposed to split tunnel but I think that is more a Mac issue than a router configuration issue.
Now, I need to find one like this one for site-to-site VPN!
Great to hear!!! Thanks for the feedback – appreciated!!
Perhaps I need to re-consider this site-to-site VPN guide as well, as quite many ppl are actually asking for it….. 🙂
Awesome. Works perfectly on the USG 50. Thanks man.
Thank you for the feedback – appreciated!!!
Take care!
Hi Ketola
Thank you for this great how to – I was able to follow everything and it’s working now.
The only thing which was different at my place is – I do have a router which makes the NAT before the Firewall.
You mentioned in the local policy that the public IP should appear – but I thought it is just the WAN address of my firewall which is connected to the router but not the real public IP.
This was then mentioned in the Zyxel how to here for all who are strugelling with the same topic: https://www.studerus.ch/de/support/knowledgebase/detail/115090
Thanks again and have fun
Roger
Thanks for this – appreciated!!!
The link will sure help someone!!
Take care!!
It works!!! Thank You!
Thank you for the confirmation!! Take care!!!
Dear Juha,
following your instructions I can establish a connection. I can access the Internet through VPN, however I cannot reach my LAN. What could be wrong?
Thanks for any hint
Andrew
Perhaps I should add that there is a Firewall rule allowing any traffic from IPSec_VPN to any destination.