This is complete step-by-step configuration instructions for setting up VPN connectivity (L2TP/IPSEC) between Zywall USG firewall and the client devices including Windows Phone, iPhone/iPad and Android or Win 10 OS.
For those not fully aware about the advantages VPN will give you – it will enable an encrypted pipeline to your home/office network, and you can use all the services/devices in your private network in safe and secure manner, without opening unnecessary ports that would increase the level of vulnerability of your private network.
Examples of VPN usage:
- Connect and use internet and online services in encrypted and secure manner from not-trusted environments like cafes and public WiFis.
- Stream freely from anywhere your private videos, view your private photos or work with any computer/document that is available in your network.
- View and access country-level regulated online materials from your VPN ‘home’ location when traveling abroad.
- Connect to you surveillance cameras, wildlife trail cameras or home alarm systems.
Find below step-by-step configuration instructions for enabling above:
Zywall:
1) Setup and ensure/add that ports required by VPN connectivity are defined and available (NO other SERVICES that are utilizing the same ports!):

2) Create VPN User (Object/User tab) and VPN Group (ObjectGroup tab), and add created user into the Group:
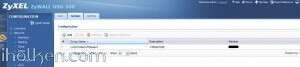
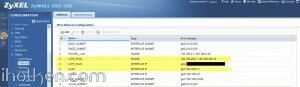
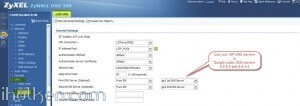
3) Create WAN, L2TP_POOL and LAN addresses accordingly (L2TP range TO BE completely outside any home/external IP range, that might be in use in either end of the VPN tunnel during VPN utilization – otherwise you may expect trouble…):
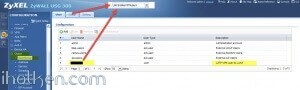
4) Create IPSEC VPN gateway (create own or utilize default available, link then to VPN connection created below):
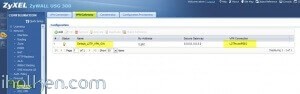
4) Detailed configuration example:
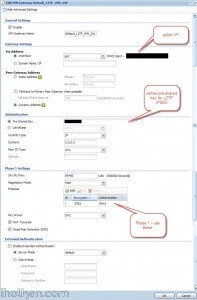
5) Create VPN connection that uses above created VPN gateway (you can utilize default available or create own):
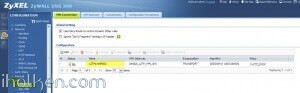
5) Detailed configuration example:
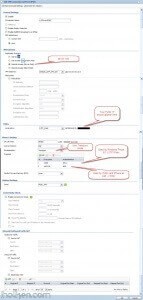
7) Create required firewall rules. Make sure VPN required services/ports are allowed (for example IKE, default rule in Zywall). Allow from IPSEC/VPN to LAN or to ANY, depending if wanted through VPN access only to LAN or also to internet:
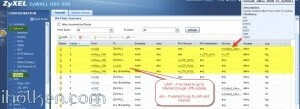
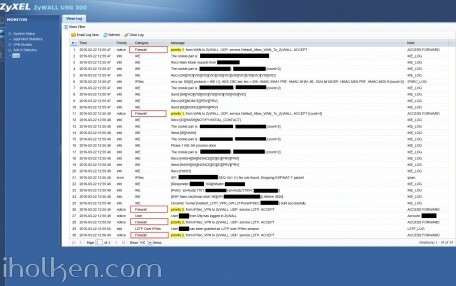
Firewall rules has critical role in establishing the tunnel and allowing the traffic through the tunnel. Please find below for VPN connection ‘negotiation handshake’ troubleshooting purposes an example of successful L2TP/IPSEC handshake flow extracted from Zywall log, and the parts where firewall rules play critical role:
If you have any issues with your firewall, please enable logging for correct steps and investigate the zywall logs – they are extremely useful.
8) Create required routing rules. (IF ‘send all traffic’ through VPN is on (meaning internet through VPN) – you also need to setup the Policy Route that is upper in the table below:
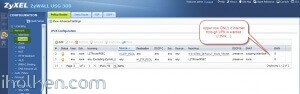
9) Keep WAN trunk and SNAT enabled:
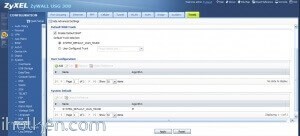
Client Machine:
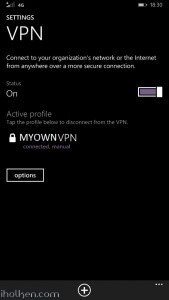
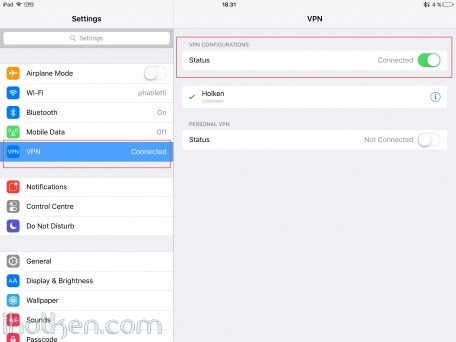
10) Configure client machine – below example Windows Phone 8.1+:
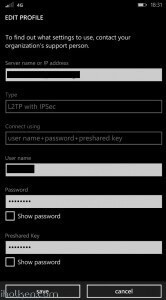
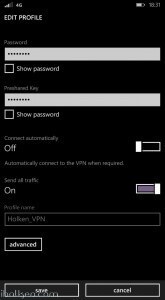
Test Connectivity:
11) Test and confirm VPN by accessing your private network through 4G VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.

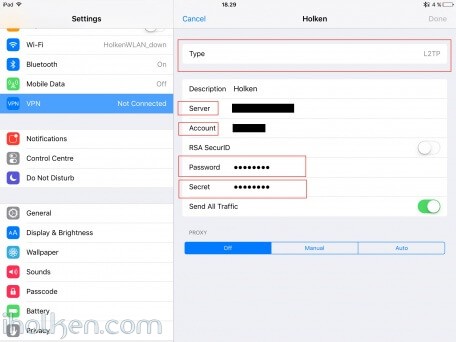
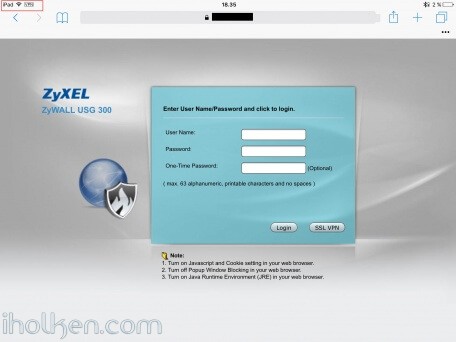
12) Configure client machine – below example for IOS (IPhone or IPad):
Test Connectivity:
13) Test and confirm VPN by accessing your private network through VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.
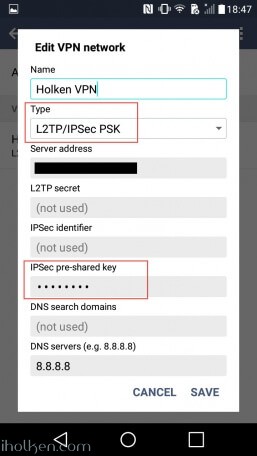
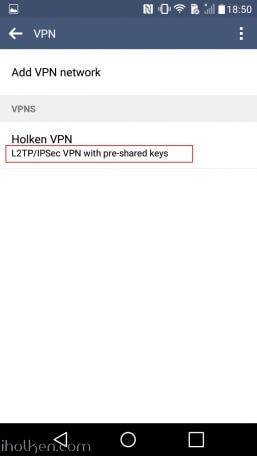
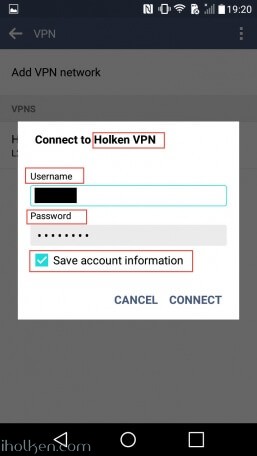
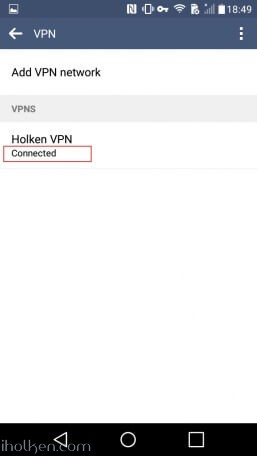
14) Configure client machine – below example for Android (Lollipop sw):
Test Connectivity:
15) Test and confirm VPN by accessing your private network through VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.
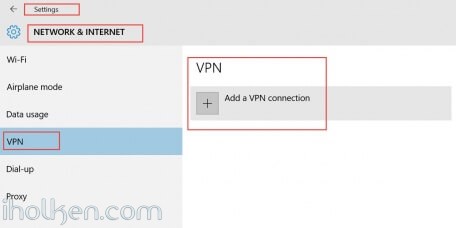
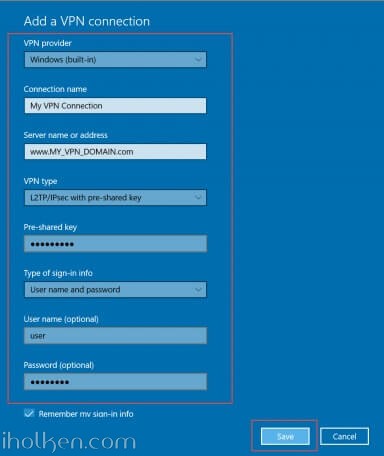
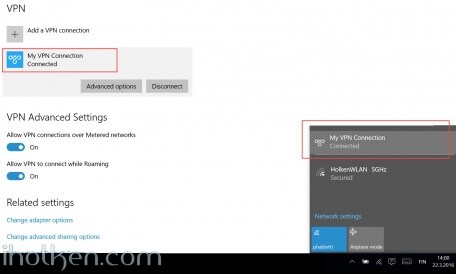
16) Configure client machine – below example for Windows 10 Operating System:
Navigate to: Start –> Settings –> Network & Internet –> VPN –> Add a VPN connection
Then give the required connection details for the connection and hit Save:
Now you are able to Connect to the VPN tunnel – through Network Settings or System Tray, and see ‘Connected’ indicator:
And that’s it!
Now you have configured the Zyxel Firewall for VPN connection with L2TP/IPSEC and client device being WP or IOS / Android Device or Win10 OS.
If this helped you in getting your VPN connection built, please drop me a post below for confirmation – Thanks!!! 🙂





Dear Juha Ketola,
Well done Juha. Thanks so much for your great instruction! You help people to solve Zywall L2TP issue.
One of minor question, I cannot ping or access my local network all of computers except internet. Would you please guide me how to fix it?
Thanks again!
Hi Alex,
Thanks for the kind words. 🙂
Regarding your issue, there can actually be many many reasons for that. Cannot list all those in here. But if we start from the most obvious issue, and I provide you couple hints to further troubleshoot your issue. Ok?
1) If you cannot access something, then something is most probably blocking you. I suspect firewall. Please enable/create a firewall rule to allow traffic from your VPN Zone to your LAN zone. That is rule #4 in my guide, if you see the pic of the firewall settings. You need to place this rule before and DENY rules you might have in your fw table, as those are processed in order, so quite up there in your list.
2) If that rule was not solving the issue, please configure all firewall rules that [BLOCK] your traffic into logging mode [LOG]. And then see [Monitoring] –> [LOG] events for any information what is the rule blocking you. That should help you in your configuration changes.
3) One other thing to check, that might cause issues: Please review your IP ranges for these 3 items, preferably they should not ever be overlapping. IF they are, you need to be careful in how you assign your IPs for devices in both end of pipes:
– Source LAN
– VPN IP pool range
– Target LAN
I’m confident this will help you to solve your issue.
Take care!
Dear Juha Ketola,
Many thanks for your prompt support! I did go through each steps under your detail instruction, but it is no luck.
Basically, it seems routing issue not my USG 200 firewall blocked L2TP VPN data to LAN 1 by disable it for checking.
I am learner and dont know how to solve the below log error. Your kindly help is highly appreciated.
1
2016-09-16 15:15:35
error
IPSec
SPI: 0x0 (0) SEQ: 0x0 (0) No rule found, Dropping UDP packet
192.168.2.107:161
192.168.1.15:1041
ipsec
Hi,
Ok…. Kindly – please double doublecheck the guide still, are you really exactly using the same settings as in my guide. And please check that they are EXACTLY as in my guide…
One example is the authentication phases and the encryptions used in phase 1 and phase 2:
Phase1:
3DES – SHA1
AES128 – MD5
Phase2:
3DES – SHA1
Use exactly those.
Same goes for firewall rules, routing rules, ports, services. If you configure everything like in my guide – it will almost certainly work. I have received hundreds of feedbacks from ppl successfully used my guide. Just be careful – you will get it to work. 🙂
Good luck.
/Juha
Dear Juha Ketola,
Thanks so much for your prompt reply once again! I did exactly using the same settings all of steps by your instruction, but still cannot access local network. As you told me that hundreds of people setup it successful and sure certainly work. So I am fully confident of your setting and try to change other parameter which you did not mention on screen. Finally I can using L2TP connection route success local LAN.
It is under the IPv4 Configuration, after disabled check-box “Use Policy Route to Override Direct Route”, then access local Lan without issue.
I dont know how to set the policy route to access local LAN through L2TP connection normally, at least I can access network computers this time. You are so smart and expert, and much better than Zywall technical support reply. Have a good day my dear friend Juha
Dear Juha Ketola,
thank you very much for this incredible HowTo. With this I was able to set up my Zywall-VPN-Access properly.
I have some questions how to set up a guest-network with a Zywall USG60 and Zyxel WLAN-APs.
Even with deep research I wasn`t able to get it working.
If you are able and willing to help I would appreciate your short reply via email to check out the conditions!
Thank you again.
Regards
Stephan
Hi Stephan,
So you tried to follow some guide like this:
http://kb.zyxel.com/KB/searchArticle!gwsViewDetail.action?articleOid=015518&lang=EN
You actually SHOULD get it to work fairly easily, as the VPN configuration in my opinion is a LOT more complex setup. 🙂
Hi,
Thank you for the good article. Have you come across this in your research?
I am having an issue with the Phase 1 proposal. I tried this order you suggested but still unsuccessful. I tried from W7SP1 and W10.
Phase1:
3DES – SHA1
AES128 – MD5
Phase2:
3DES – SHA1
The log output from the USG20w-vpn (latest firmware) is:
Send:[NOTIFY:NO_PROPOSAL_CHOSEN]
The cookie pair is: 0x41e35cab0dd39ec / 0x7182fv3b8f771eb
Recv IKE sa: SA([0] protocol = IKE (1) AES CBC key len = 256, HMAC-SHA1 PRF, HMAC-SHA1-96, 384 bit ECP, AES CBC key len = 128, 256 bit ECP, 2048 bit MODP, 3DES, 1024 bit MODP’).
any thoughts?
Thanks.
Hi!
Interesting – I do know that those phase1 options work for sure with win7 and win10….
Are you sure that you have configured your vpn client right? With L2TP-IPSEC with pre-shared key? I would very much like to blame your client end, if your vpn config is exactly as I have outlined in my guide.
You could try: 1) any other device / OS you could try to configure the client? Like your phone? 2) cycling through all the phase1 encryption options in config – but I still doubt that the issue is not there…
Doublecheck everything in your config. Have you configured firewall rules accordingly?
And no – I have not stumbled earlier into your issue in any setup, phase 1 handshake is not usually the one causing trouble…
thanks for the follow up.
not sure what my issue was but I changed phase 1(gateway) to 3DES SHA1 only and phase 2 (connection) to 3DES, AES128 and AES256 all SHA1.
both W7 and W10 connect.
all I need to do is figure out how to get the local lan. I get internet access but not local systems.
Thanks. Good job with the details.
Hi Juha,
our firewall is running perfectly, my question is ;
if i make a vpn connection , i can connect to my servers ( with the right ip adress ) , but it does not regonize the netbios name ( for example server1 = 170.23.3.1 ) we do not use wins , is there another option for this to make it possible ?
thanks
Hi Patrick,
Please use the DNS server inside your Zywall, and configure there the relationship between desired server name/address, and the associated IP address.
Then you need to define the Zywall LAN IP as the first DNS server for those LAN ports or VPN gateway, and the public DNS server in use as the second DNS server.
This way it will try to find the IP based on the name first from Zywall and if not found, only then from public DNS server.
Hope this helps you.
Hi Juha,
Thanks, i just changed the first DNS with the inside DNS from the Zywall, this was enough for us.
thanks again my friend,
Patrick
Hi Juha,
Great post! Could you write an article about how to route only specific website through the VPN tunnel?
Thanks!
Regards,
Chan
Hey Chan!
Thanks for the compliment!
Do you mean that you want to establish a VPN tunnel, but direct the traffic only for certain IP’s through the tunnel? This is called split tunneling, and is defined on the VPN client end. There are just too many clients to cover, so I don’t see this feasible.
I’ve done this kind of setups myself using Microsoft CMAK tool, and created VPN installation packages for Windows environments – they do exactly this. Also many VPN clients allow you to define IP ranges for the VPN tunnel… So as said, there are many options available for you to choose.
But keep in mind, that in quite many cases, split tunneling is not a wanted scenario – and all traffic is wanted to go through the secure VPN tunnel.
/Juha
Dear Juha,
thanks a lot for the great guide.
I setup all systems as you showed in your guide, but experience a problem with connecting my iPad:
It establishes the tunnel (exactly as shown in your logfile), but then it seems to disconnect (there ist no user connecting to the zywall, and the ipad says “server not responding”). Do you have any clue as to how to solve this problem?
Hi,
have you tried any other clients? Like Windows native VPN client? Or client in Android? Just wondering if this is specific to IPAD or a real issue.
So if you check the logs, what is actually the exact point – when the connection gets disconnected?
Is it right after when you get into your log:
– ….dynamic tunnel built successfully
– ….user logged in zywall
– ….user granted an L2TP over IPSEC session
Or after something else?
Hi,
thanks for your reply.
This happens with VPN Clients from iPad / iPhone and native Win10.
The connection gets disconnecte right after the message “dynamic tunnel built successfully”.
Do you have any clou on where to start looking?
Hi Christian,
hmmm – sounds like firewall issue.
Are you having in place the fw rules as they are in my guide above?
Especially the Rule #2 in my fw listing above?
That rule is triggered right after the TUNNEL is built successfully. If you don’t have that rule in place – your connection will be disconnected.
If above hint won’t solve the issue, please temporarily enable logging in your zywall firewall rules to EVERY ROW where you have DENY, and try VPN connection – then check logs row by row – and see where your VPN connection gets throwed out.
Hope this helps.
Help 😉 So I have followed your steps and triple checked everything (I must be missing something though). I am able to make a VPN connection into my network, I am able to also browse the internet through my VPN connection. I do obtain an IP address within the range I have specify. I am unable to ping, access network shares or web sites of any of my clients that are internal. I am at my wits end on getting this enabling this.
My client is a Win10 using the Microsoft internal VPN client.
Your guide has been a vaulable resource on me getting this far. Thank you for sharing your knowledge.
Any help or guidance that you can provide?
Hey Rick, welcome to the world of VPN!
Ok, let’s first tackle the obvious:
1) Have you ensured that the IP ranges are not overlapping in either side of the VPN tunnel – or with the VPN client range itself?
2) Please inspect firewall and routing rules. Because – if you cannot connect to something – it is either because it is denied (firewall) or that it cannot find the route (you have some strange routes defined). And yes – you need to specifically allow traffic from VPN tunnel to the needed LAN range(s).
If above hints won’t solve the issue, please temporarily enable logging in your zywall firewall rules to EVERY ROW where you have DENY, and try connecting – and inspect the logs. Or just temporarily quickly carefully disable fw, and test the access (and then enable fw). If no luck, check then routing rules. If still no luck – review your local hosts file – or ensure that you are not behind some limited network like company network or similar.
Good luck – update me if u figure it out!!
Hi,
I have successfully setup this VPN and can access and ping the local network however no matter what I try I cannot access the internet when VPn’d in. I have added the firewall rule as suggested and selected any but still no way out
any help would be appreciated