This is complete step-by-step configuration instructions for setting up VPN connectivity (L2TP/IPSEC) between Zywall USG firewall and the client devices including Windows Phone, iPhone/iPad and Android or Win 10 OS.
For those not fully aware about the advantages VPN will give you – it will enable an encrypted pipeline to your home/office network, and you can use all the services/devices in your private network in safe and secure manner, without opening unnecessary ports that would increase the level of vulnerability of your private network.
Examples of VPN usage:
- Connect and use internet and online services in encrypted and secure manner from not-trusted environments like cafes and public WiFis.
- Stream freely from anywhere your private videos, view your private photos or work with any computer/document that is available in your network.
- View and access country-level regulated online materials from your VPN ‘home’ location when traveling abroad.
- Connect to you surveillance cameras, wildlife trail cameras or home alarm systems.
Find below step-by-step configuration instructions for enabling above:
Zywall:
1) Setup and ensure/add that ports required by VPN connectivity are defined and available (NO other SERVICES that are utilizing the same ports!):

2) Create VPN User (Object/User tab) and VPN Group (ObjectGroup tab), and add created user into the Group:
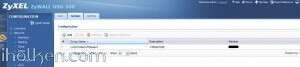
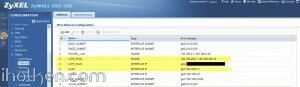
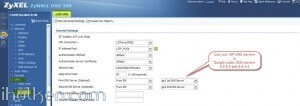
3) Create WAN, L2TP_POOL and LAN addresses accordingly (L2TP range TO BE completely outside any home/external IP range, that might be in use in either end of the VPN tunnel during VPN utilization – otherwise you may expect trouble…):
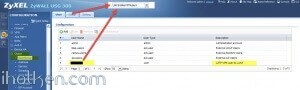
4) Create IPSEC VPN gateway (create own or utilize default available, link then to VPN connection created below):
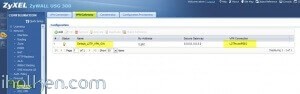
4) Detailed configuration example:
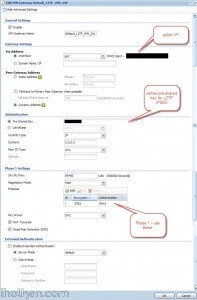
5) Create VPN connection that uses above created VPN gateway (you can utilize default available or create own):
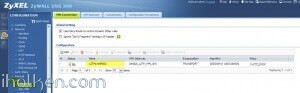
5) Detailed configuration example:
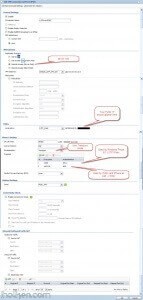
7) Create required firewall rules. Make sure VPN required services/ports are allowed (for example IKE, default rule in Zywall). Allow from IPSEC/VPN to LAN or to ANY, depending if wanted through VPN access only to LAN or also to internet:
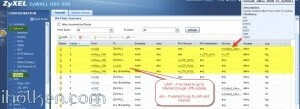
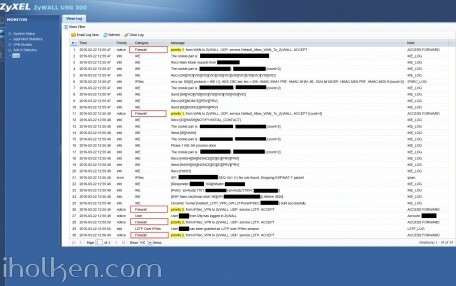
Firewall rules has critical role in establishing the tunnel and allowing the traffic through the tunnel. Please find below for VPN connection ‘negotiation handshake’ troubleshooting purposes an example of successful L2TP/IPSEC handshake flow extracted from Zywall log, and the parts where firewall rules play critical role:
If you have any issues with your firewall, please enable logging for correct steps and investigate the zywall logs – they are extremely useful.
8) Create required routing rules. (IF ‘send all traffic’ through VPN is on (meaning internet through VPN) – you also need to setup the Policy Route that is upper in the table below:
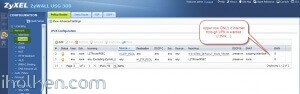
9) Keep WAN trunk and SNAT enabled:
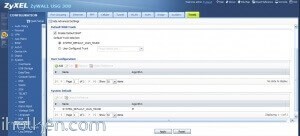
Client Machine:
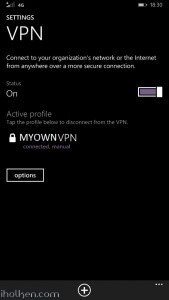
10) Configure client machine – below example Windows Phone 8.1+:
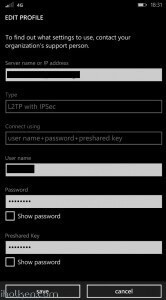
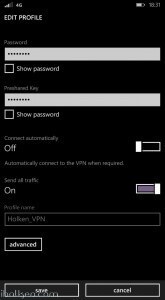
Test Connectivity:
11) Test and confirm VPN by accessing your private network through 4G VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.

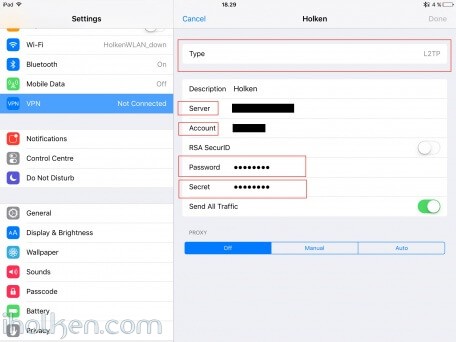
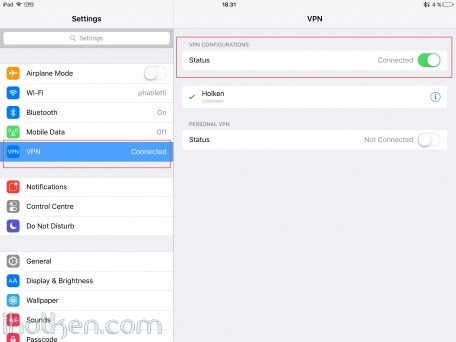
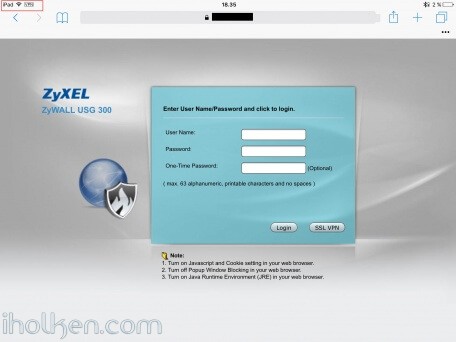
12) Configure client machine – below example for IOS (IPhone or IPad):
Test Connectivity:
13) Test and confirm VPN by accessing your private network through VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.
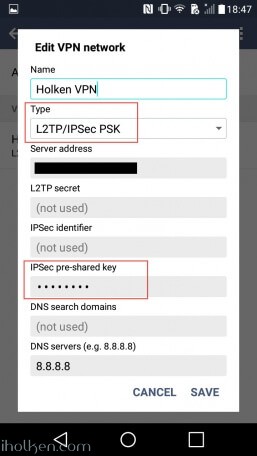
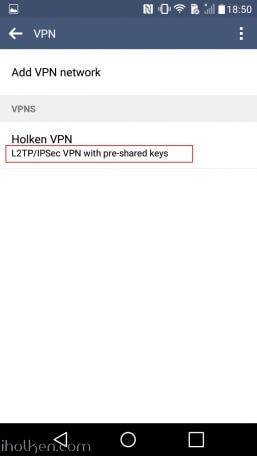
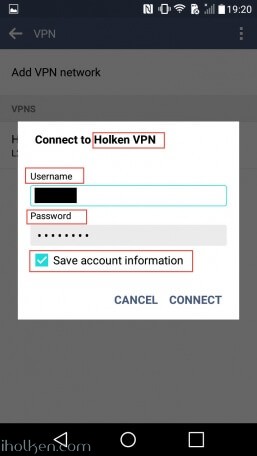
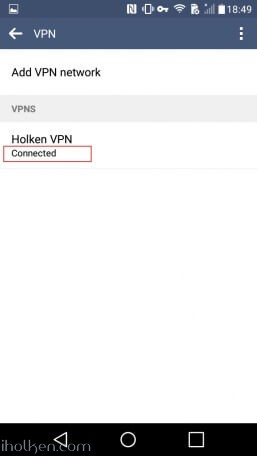
14) Configure client machine – below example for Android (Lollipop sw):
Test Connectivity:
15) Test and confirm VPN by accessing your private network through VPN connection (lock indicator). Also internet addresses are available through VPN, if allowed in firewall and routing table.
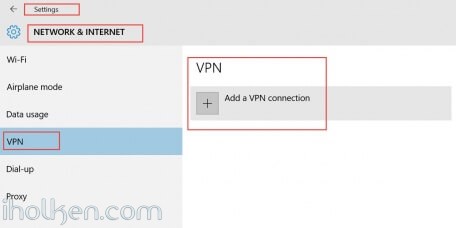
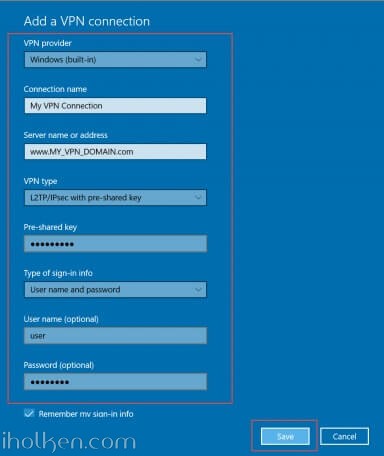
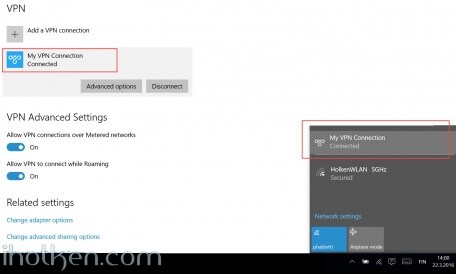
16) Configure client machine – below example for Windows 10 Operating System:
Navigate to: Start –> Settings –> Network & Internet –> VPN –> Add a VPN connection
Then give the required connection details for the connection and hit Save:
Now you are able to Connect to the VPN tunnel – through Network Settings or System Tray, and see ‘Connected’ indicator:
And that’s it!
Now you have configured the Zyxel Firewall for VPN connection with L2TP/IPSEC and client device being WP or IOS / Android Device or Win10 OS.
If this helped you in getting your VPN connection built, please drop me a post below for confirmation – Thanks!!! 🙂





Do you have a upto date version of this. Seems like many firmwares ago.
Br
Rutger
Hi – The model in the guide is Zywall USG 300 and the firmware is 3.30 (AQ.7), which is the latest available firmware for this model released this year. USG 300 is on the high end side of the Zywall firewalls, at least based on the retail price. So not sure now if that is the reason for the UI difference now that you are experiencing?
Which zywall model are you having? The basic things needed for setting up VPN for thease devices are the same, and a friend of mine was able to setup VPN for new USG 40 model wihout issues following this guide. So you most probably have all the same things in your UI, just hidden under diff menus or structures…
So, If I read your article a site-to-site VPN combine with a L2TP VPN is not possible?
Hi Vincent,
Thanks for your question – but why would you think it is like that? Can you elaborate a bit more what you mean? Even though I don’t have site-to-site VPN perspective / configuration covered in my article, it does not mean that it isn’t possible. I guess my post here is covering a bit more the consumer scenario for VPN usage, in a bit more detailed manner than zyxel’s own guides. So that even the inexperienced user could potentially enjoy the benefits of own VPN connection.
In principle it would be bad for business from Zywall perspective, if customers couldn’t have VPN tunnel to company branch office, while branch office is connected to company HQ with site-to-site VPN.
Hi Juha,
many thanks for this how-to, it’s by the far the best I’ve found so far. However, I’ve tried for hours to set this up without luck.
Configured per your example.
Having USG 200 on latest FW level (already tried with older versions before).
I see the firewall allowing all the required traffic on ports 500, 4500 and 1701. I have enabled to log all blocked traffic, nothing related is blocked.
Tunnel seems to get build up successfully but then ends.
iPhone says quite some time later that authentication failed, while the credentials are correct (if I change to a wrong password or wrong PSK on my iPhone then an error is displayed very quickly).
Here some key log entries from the USG:
Phase 1 IKE SA process done
…
Priority:4 from IPSec_VPN to Zywall, UDP, service L2TP-UDP, ACCEPT
…
[ESP aes-cbc|hman-sha1-96][SPI……
…
Dynamic Tunnel [RAS_L2TP_VPN-GQ:L2TPoverIèPSEC:…] built successfull
…
IKE Recv:[HASH][DEL] [count=2]
IKE Received delete notification
…
IPSec SPI: 0x0 (0) SEQ:0x0 (0) No default rule found, Dropping UDP packet [count=9]
…
Do you by any chance have some hint for me?
Regards,
Claudio
Hi Claudio,
Thanks for your comments!
You most probably have an issue with your firewall configuration (rule 2 in fw example in guide). Please doublecheck firewall rules and order of rules. I actually updated above guide (step 7) with example handshake flow for establishing the VPN connection. Please take a look.
You have an issue with step26 in the log example. You need to allow the traffic:
FROM: IPSEC_VPN
TO: Zywall
IPV4 Destination: L2TP_WAN (wan port utilized during VPN)
Service: L2TP (l2tp ports – UDP1701)
Once you fix that – your connection should be established correctly.
Please let me know the results!
/Juha
Hi Juha,
thank you for the fast reply.
FW rules seem to be correct. My logs are matching your logs until I would expect the user authentication log entry:
…
…
IKE – [Responder x.x.x.x][Initiator:x.x.x.x]
IKE – [Policy: ipv4(udp:x.x.x.x)-ipv4(udp:x.x.x.x)]
IKE – [ESP aes-cbc|hmac-sha1-96][SPI 0x…][Lifetime 3620]
IKE – Dynamic Tunnel [RAS_L2TP_VPN-GW:L2TPoverIPSEC 0x…] built successfully
Security Policy Control – priority: 3, from IPSec_VPN to ZyWall, UDP, service L2TP-UDP, ACCEPT
(…then 30 seconds no log entry…)
IKE – The cookie pair is: 0x… / 0x…
IKE – Recv:[HASH][DEL] [count=2]
IKE – Received delete notification
IKE – The cookie pair is: 0x… / 0x…
IKE – ISAKMP SA [RAS_L2TP_VPN-GW] is disconnected
As you can see, the tunnel is built and L2TP traffic accepted. But I never see any authentication record. And 30 seconds later it seems to run into a timeout.
/Claudio
This is getting interesting…. Any chance you could try some other client device? Like laptop or Android? And which Iphone version you have? Just trying to figure out are all clients in your config failing – or only the Iphone…..
Update**
Please check also your phase 2 encryption algorithms, do you have those in same order as I have?
1. 3DES…
2. AES…
Reason for this is, that I tested Ipad4 and Iphone 6s, and both were working and using [ESP 3DES SHA1] – if you followed my guide. However your log suggests that you use [ESP AES SHA1].
Try to get into your log following line:
[ESP 3des-cbc|hmac-sha1-96]
Perhaps there is the critical difference here. There has been some variation with iphone models and phase2 support. Please follow my guide exactly, and test.
Thanks.
/Juha
I use an iPhone 6s and an old iPad, both with IOS 9.2.1 (but also tested it some months ago with IOS 8.x, before I gave up the first time). No Android device around me. Will need to test it with a laptop…
I have following phase 2 algorithms:
#1 AES256 / SHA1
#2 AES128 / MD5
#3 3DES / SHA1
Tried now also with following:
#1 3DES / SHA1
#2 AES128 / MD5
… result is exactly the same.
Will report back once I have tested with my laptop during coming days.
Thanks for your help.
Ok!
Ok, tried now with Windows 7.
Exactly the same result like on iOS. Dynamic tunnel is built successfully, followed by L2TP traffic accepted. After half a minute or so it times out.
The Win7 client connects to the USG and then displays “Verifying username and password…” until it times out. In the debug logs on the client I found error 718 which is a PPP timeout (https://support.microsoft.com/en-us/kb/923944), nothing more.
Can’t help the feeling that this is some NAT or routing issue, while I can’t find any misconfiguration.
Ok. Network configs can be extremely tricky to troubleshoot… So you have NAT in between endpoints in your tunnel? I guess you have enabled NAT-T (requires port 4500 to be available!!!!!) and DPD in your VPN gateway phase1 settings? I really would like to see this solved….
No, mixed it up, no NAT in the tunnel used.
Most probably the easiest problem, and most evident problem could be – that you have in between your client and zywall a device (eg. router) that does not support vpn passthrough. Have you checked this one already?
Yes, checked this as well. I have a DOCSYS cablemodem/router. It is configured as a bridge and doesn’t allow me in this mode to configure VPN passthrough. I temporary configured it to router mode where VPN passthrough was enabled by default. Also no luck.
When it is in bridge mode, I connected the PC directly to the modem as well. Strangely my USG and my PC received IP addresses from different ranges:
Router x.x.195.48 255.255.255.0
PC x.x.228.225 255.255.248.0
Tried VPN connect without success.
When it is in bridge mode, both USG and PC got a 192.168.0.x/24 address which I haven’t already used on the internal network. Also tried VPN, also without success.
What I will try next is to disconnect the USG from internet and configure a static WAN network. Then connect the PC with a static IP to the WAN port and again test the VPN connection. Just to be sure it’s really not caused by this cablemodem in some way…
Ok, I think it is good idea to try private wan with usg. That nicely eliminates potential cable modem issue or anything fuzzy caused by your Internet Service Provider – and you can focus to correct parts in your network setup.
Hi Juha,
sorry for not responding with an update for so long. I had other priorities past months (“family expansion”).
I just like to let you know that it is now working. I only did following changes:
1) Upgraded firmware of my USG210 to 4.20(AAPI.0) which contains quite a lot of fixes including VPN related ones.
2) I moved the L2TP pool range.
Before I had something like:
– 192.168.10.0 (LAN)
– 192.168.20.0 (L2TP) – Pool was from .11 to .30
– 192.168.90.0 (DMZ)
Now I have something like:
– 192.168.10.0 (LAN)
– 192.168.90.0 (DMZ)
– 192.168.100.0 (L2TP) – Pool is now from .1 to .10
Thanks again for your support and this great manual!
Hi Claudio!!
Great to hear – thanks for confirmation!
Take care!!
I am impressed and very thankful for this very detailed and comprehensive overview and “How-to”! It helped me to set up VPN in 30 minutes after having spent days and hours reading through many half-hearted websites.
Really appreciated!
Thanks Daniel for the feedback – really appreciated on my side as well! And it is always nice to hear good feedback and success stories. I myself enjoy reading comprehensive ‘HOW-TO’ -guides, so this is my way of trying to return the favor to all! 🙂
/Juha
Mr Ketola,
Thank you so much for such a comprehensive list on configuration. I was so close with other guides but you provided the additional routing rules not covered in any of the other posts I have found. This allowed me to complete and successfully configure my VPN.
again thank you
Hi Brad!
Thank you for the feedback – I’m glad it worked out for you. It seems security is taken more seriously nowadays – as people are showing more and more interest in vpn solutions. It’s great to be able to support and help ppl in that journey!
/Juha
Ciao, Juha.
Thank you so much for great manual. I spend a lot of time by trying to set it up. You’ve helped me very much.
Once again, Thank you 😉
Hi Francis,
Humble thanks for the kind words!!
/Juha
I have this bookmarked. I actually have the Zywall 110, but just barebones getting the vpn up and running, this works (using Windows 7/10).
I’m having an issue with getting the network to be accessible to the VPN clients. But I’m probably missing one small thing.
It did save me time.
Nice work.
Hi Travis!!
Thank you for the feedback – appreciated.
And I hope you were able to iron the last wrinkles you had there…
/Juha
Really appreciated !!!! I am impressed and very thankful for this very detailed and comprehensive overview and “How-to”! It helped me to set up VPN in 30 minutes after having spent days and hours reading through many half-hearted websites.
Thanks Jafar – great to hear it worked out for you!!
And special thanks for leaving confirmation!
Take care!
I have an rdp server that I need to connect with a vpn to a zyxel router. The server has a wan address -no router. I need that people rdpin into the zyxel ip should be forwarded to the rdp server that is connected via vpn to the zyxel. I want all traffic from that rdp to pass through the zyxel. Can i make it site to site? I found someone who setup client on the server to site -zyxel and it worked. But it was slow and I lost the configuration due to a failed router .
Hi Ben….. Oh man – trying to figure out someone else’s config issues in network setup is a nightmare….
All I can say is, that site-to-site should be possible and work nicely in nearly every setup with devices capable of establishing such connection on both ends of the line… You do need some routing rules and hopping, and drill holes to your firewalls, but eventually it should be possible.
Good luck for your journey – quite impossible to provide deeper solutions for you. Hope you figure it out.
Thanks.
we have a usg-1000 firewall , i already tried everything for setting up a L2PT connection, internal it does work , but from the outside i can not connect. already busy with this 3 day,s and already giving it up :)))
can someone help me ( i can give my remote usg-1000 ip adress for checking it up ) it is a test envirement , so everything can be changed if possible.
please email me at : xxxxxxx@xxxxxx (edited – email removed by Juha)
With some really great help from Juha i manage to make the VPN up and running really a big thanks from here … the main problem is that i made some NAT entries for the VPN , after removing this entries and some changes it,s running.
Nice blog
greetings from Holland
Patrick